# Spike Security
When you're dealing with financial data security is of the utmost concern
Our infrastructure conforms to industry best practices which includes secure https communications (with JWT auth), encrypt at rest data, and all servers are secured within an AWS VPS. This security guide describes our architecture in depth and lists the independent audits which we've passed. It is kept updated whenever we undertake new security measures.
# Independent Security audits
- Spike's network has undergone 2 penetration and vulnerability scans by independent security consultancies: Mobius Consulting (opens new window) and Exocet Security (opens new window).
# Mobius Consulting
The summary of Mobius' findings were:
Overall, the SpikeData web applications and API’s were found to have a robust security posture.
- full details are available in the attached report
# Exocet Securities
The summary of Exocet's findings were:
In our assessment this is a highly secure system with no readily apparent or exploitable security flaws.
- full details are available in the attached report
Remedial action taken by Spike in response to Exocet Security recommendations:
- Implement 2fa with sshd service
- we have implemented 2fa on all our EC2 servers
- this requires a 2fa device to be present in order to ssh into a server
- see
EC2 instance securitybelow for an example ssh session commencement
- Implement the advised click jacking countermeasure
- We've implemented
X-Frame-Options: sameoriginandContent-Security-Policy: frame-ancestors 'self'headers on all responses all our sites - as per https://www.netsparker.com/blog/web-security/clickjacking-attacks/ (opens new window)
- We've implemented
- Put measures in place to detect hack attempts and ban IPs
- we have switched to using Cloudflare in front of all public services (app.spikedata.co.za & api-v6.spikedata.co.za)
- this provides both optimization benefits (CDN / cacheing) as well as security (threat detection and DDoS protection)
- the latest Cloudflare report (Feb 2020) is attached
- Implement 2fa with sshd service
# Spike API VPC design and security
Diagram: Spike Infrastructure 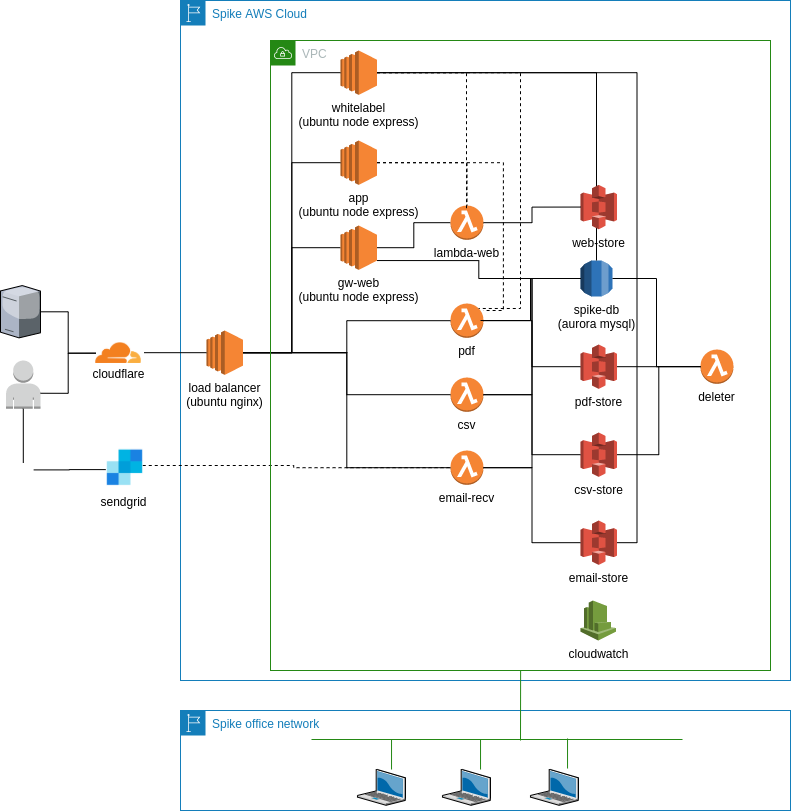
Highlights
- all traffic from user and client apps to {app, whitelabel, api-v6 }.spikedata.co.za is encrypted (with TLS 1.3)
- There is only one publicly routable server - the load balancer - all other servers have private VPC addresses
- The VPC is only accessible from the Spike Office Network.
- We use IAM policies to control which resources may be accessed by developer accounts
- The s3 stores are used for temporary storage of pdfs, csvs, and screenshots (web scraping). See private data management below.
- Cloudwatch is used for logging by all lambda and web services. All requests and responses are sanitized by the
Spike Shape Systemin order to prevent private information (like passwords) from being logged. We use a maximum 1 week retention period on all log streams.
# Private data management
Pdfs which fail to process are collected in the pdf-store for further analysis by Spike developers. We have internal error diagnostics tools that are able to check the error queue without needing direct access to the pdfs. In some cases it possible to dismiss the error (and delete the pdf from the store) without needing further analysis (e.g. when junk pdfs are detected).
Pdfs that expose edge cases in existing parsers as well as new unsupported statements must be downloaded to a development laptop for further fault diagnosis and development. After the pdfs have been resolved they are automatically deleted from developer laptops.
We have developed a sophisticated series of automated unit tests which allows us to support both rapid turnaround time on the deployment of fixes and new parsers as well as preventing errors. All tests must pass before a deployment can proceed.
The lambda-deleter takes care of removing resolved errors from the various S3 stores.
# Spike security best practices
EC2 instance security
- limit attack surfaces
- limit publicly accessible services
- most servers are not publicly accessible
- we use IP filters to limit access to Spike network IPs (+ VPC IPs)
- ip security filters
- disable all ports except ssh & http(s)
- ssh security
- use per-developer ssh keys + 2fa
- example login session:
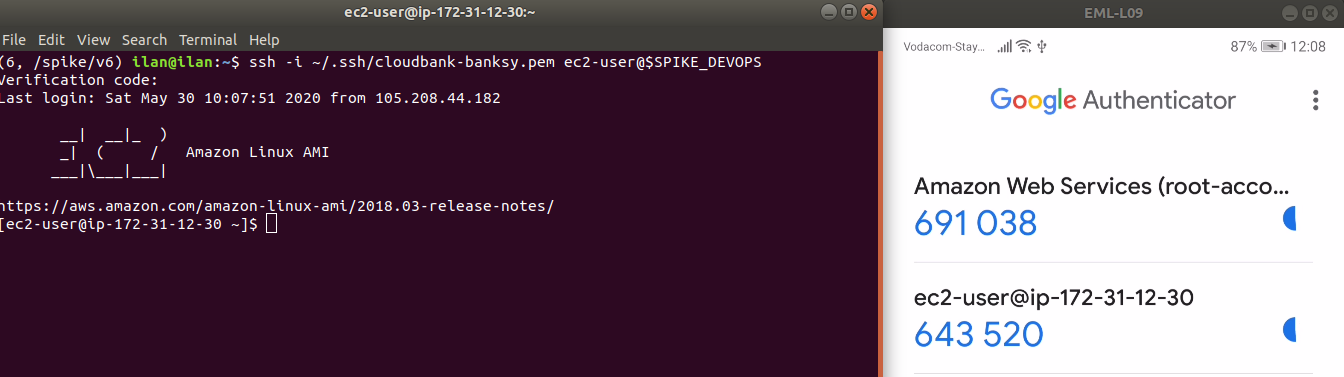
- OS security
- Spike uses unattended-upgrades (opens new window) to perform daily security patching of all ec2 boxes
RDS & S3 security
- Spike uses managed services for storage (S3) and databases (AWS Aurora)
- AWS manages uptime, patching, and security updates of the underlying infrastructure all of which is HIPAA / PCI DSS certified
- Spike uses AWS IAM to grant individual developers permission to these resources as required
AWS lambda
- Spike makes extensive use of AWS Lambas
- Spike lambda functions include pdf parsing, email receipt attachment extraction and parsing, web scraping, as well as various internal cron jobs
- Lambdas by their nature are short-lived, single invocation services which do not open additional network listening ports
- Hence these services are not susceptible to remote root compromise attacks
- AWS Lambda is HIPAA / PCI DSS certified
General node.js software development security
- Spike makes use of various open source packages available from the npm registry
- Spike regularly reviews the packages chosen by our developers and makes use of
npm auditto keep abreast of security vulnerabilities in the packages which we depend on.- our policy is to remove redundant, obsolete, and unmaintained packages - e.g.
requesthas been replaced byaxios) - we keep dependencies updated to the latest versions except where this causes dependency clashes with dependencies (e.g.
chalk 2) - we use a mono-repo design so that all
devDependenciescan be administered from a single location and dependency clashes can be resolved more readily through the use of theyarn.lockfile
- our policy is to remove redundant, obsolete, and unmaintained packages - e.g.
- More generally, Spike strives to keep up to date with the ECMA script language changes in order to make use of emerging idiomatic best practices and has ported most codebases to TypeScript to take advantage of the benefits of static typing for managing larger codebase and teams.
Developer machine antivirus
- Spike developers run the latest Ubuntu Linux
- Antivirus scanning is performed by ClamAV (opens new window)
# Resources
- https://aws.amazon.com/compliance/hipaa-compliance/ (opens new window)
- https://aws.amazon.com/compliance/pci-dss-level-1-faqs/ (opens new window)
- https://cheatsheetseries.owasp.org/cheatsheets/Nodejs_security_cheat_sheet.html (opens new window)
- https://owasp.org/www-pdf-archive/OWASP_SCP_Quick_Reference_Guide_v2.pdf (opens new window)
- https://support.cloudflare.com/hc/en-us/articles/115002059131-Understanding-your-Site-Protection-Options (opens new window)
- https://www.linux.com/topic/desktop/security-tools-check-viruses-and-malware-linux/ (opens new window)